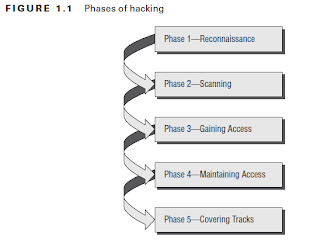
Remember this Rules:
1. If a hacker wants to get inside your system, he/she will and there is nothing
2. The only thing you can do is make is harder for him to get in
What is the purpose of security?
CIA
• The purpose of security is to insure the Confidentiality, Integrity, and Availability of assets.
http://www.mindcert.com/resources/MindCert_CEH_Ethical_Hacking_MindMap.pdf
And today, http://media.hacking-lab.com/largefiles/livecd/v5.26
I really want become a Penetration Tester(pentester)
I will have CEH. I think so. Believe me, friends
hb me, Enjoy!
Thursday, October 28, 2010
Monday, October 25, 2010
Try Harder
Yes, Try Harder...
From the first time it was uttered it has become our mantra,
and now, Offsec students Worldwide attribute the Try Harder lifestyle to the Offsec way.
Offensive Security is known for its hardcore security classes.
When you are at the pinnacle of pain begging for one hint most students receive the hint
Try Harder.....
Source: http://www.offensive-security.com/tryharder.php
thanks!!!
From the first time it was uttered it has become our mantra,
and now, Offsec students Worldwide attribute the Try Harder lifestyle to the Offsec way.
Offensive Security is known for its hardcore security classes.
When you are at the pinnacle of pain begging for one hint most students receive the hint
Try Harder.....
Source: http://www.offensive-security.com/tryharder.php
thanks!!!
Tuesday, October 19, 2010
Some example about NMAP (Nmap Scripting Engine, Conflicker, Kaspersky)
Complete Examples with Nmap Script Engine(NSE)
nmap -sC example.com
A simple script scan using the default set of scripts.
nmap -sn -sC example.com
A script scan without a port scan; only host scripts are eligible to run.
nmap -Pn -sn -sC example.com
A script scan without host discovery or a port scan. All hosts are assumed up and only host scripts are eligible to run.
nmap --script smb-os-discovery --script-trace example.com
Execute a specific script with script tracing.
nmap --script snmp-sysdescr --script-args snmpcommunity=admin example.com
Run an individual script that takes a script argument.
nmap --script mycustomscripts,safe example.com
Execute all scripts in the mycustomscripts directory as well as all scripts in the safe category.
Scan Conflicker
Use more:
nmap -PN -T4 -p139,445 -n -v --script=smb-check-vulns --script-args safe=1 [target]
nmap -PN -T4 -p139,445 -n -v --script smb-check-vulns,smb-os-discovery --script-args safe=1 [target]
Or
# Run the scripts against host(s) that appear to be Windowsnmap --script p2p-conficker,smb-os-discovery,smb-check-vulns --script-args safe=1 -T4 -vv -p445 [target]nmap -sU -sS --script p2p-conficker,smb-os-discovery,smb-check-vulns --script-args safe=1 -vv -T4 -p U:137,T:139 [target]
# Run the scripts against all active hosts (recommended)nmap -p139,445 -vv --script p2p-conficker,smb-os-discovery,smb-check-vulns --script-args=checkconficker=1,safe=1 -T4 [target]
# Run scripts against all 65535 ports (slow)nmap --script p2p-conficker,smb-os-discovery,smb-check-vulns -p- --script-args=checkall=1,safe=1 -vv -T4 [target]
# Base checks on a different ip address (NATed)nmap --script p2p-conficker,smb-os-discovery -p445 --script-args=realip=\"192.168.1.65\" -vv -T4 [target] Nmap againts KIS, Port scan First sorry, because this thread could be off topic but i dont know where to post it.
I used nmap to scan ports from work to home.
I used some different techniques to test kis firewall (6.0.2.614 build)
I was connected to home with realvnc and i disabled block ip in IDS. So 5800 and 5900 ports are detected sometimes.
When Kis feels the scan I loose the connection.
STEALTH MODE ON nmap -sT -PA -PE -v -T 3 x.x.x.x Not shown: 1695 filtered ports PORT STATE SERVICE 5800/tcp open vnc-http 5900/tcp open vnc Warning yes nmap -sF -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are closed Warning no nmap -sX -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are closed Warning no nmap -sN -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are closed Warning no nmap -sS -PA -PE -f -v -T 3 x.x.x.x Host seems down. If it is really up, but blocking our ping probes, try -P0 Warning no nmap -sS -P0 -f -v -T 3 2123 x.x.x.x All 1697 scanned ports on 212.21.239.132 are filtered Warning no nmap -sS -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are filtered Warning yes. nmap -sS -P0 -v -T 3 x.x.x.x Not shown: 1696 filtered ports PORT STATE SERVICE 5900/tcp open vnc Warning yes nmap -sT -P0 -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are filtered
Warning yes nmap -sT -P0 -v -T 2 x.x.x.x Discovered open port 5900/tcp on x.x.x.x Discovered open port 5800/tcp on x.x.x.x Completed Connect() Scan at 18:33, 1499.19s elapsed (1697 total ports) Not shown: 1695 filtered ports Warning no nmap -sT -p 1-120 -PA -PE -v -T 2 x.x.x.x Host x.x.x.x appears to be up ... good. Interesting ports on x.x.x.x : All 120 ports are filtered Warning no STEALTH MODE OFF nmap -sS -PA -PE -v -T 3 x.x.x.x Not shown: 1687 closed ports PORT STATE SERVICE 135/tcp filtered msrpc 136/tcp filtered profile 137/tcp filtered netbios-ns 138/tcp filtered netbios-dgm 139/tcp filtered netbios-ssn 445/tcp filtered microsoft-ds 1110/tcp open nfsd-status 3389/tcp open ms-term-serv 5800/tcp open vnc-http 5900/tcp open vnc
Warning yes nmap -sT -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are filtered Warning generic host nmap -sF -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are closed Warning no nmap -sX -PA -PE -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are closed Warning no nmap -sN -P0 -f -v -T 3 x.x.x.x All 1697 scanned ports on x.x.x.x are open|filtered Warning no nmap -sT -P0 -v -T 3 x.x.x.x Interesting ports on x.x.x.x : Not shown: 1697 filtered ports Warning no nmap -sA -PA -PE -v -T 3 x.x.x.x Host 212.21.239.132 appears to be up ... good. All 1697 scanned ports on 212.21.239.132 are Unfiltered Warning no I want to demostrate that Kis doesnt detect some. port scans or doesnt alert me. This is a whist for MP3 or Kis 7. I want to know or can know when somebody scan one port of my computer.
Soure:
http://nmap.org/book/nse-usage.html
http://forum.kaspersky.com/index.php?showtopic=32947&st=0&p=292135&#entry292135
thanks!!!
And Happy Women's Day!
Health and have a fun..
How to add a static entry in the ARP table
In a switched LAN that you can listen to traffic sniffers and get the same results as if the network was on a hub. Attacks such as ARP Poisoning is effective when the system lets you change the MAC of the default port dynamically.
Put another way, in a switched network can sniff our traffic safely if we are not statically set the default gateway entry.
This can be done, as the operating system, in the following ways:
In Windows 2008, Vista & 7:
netsh interface ipv4 add neighbors "Local Area Connection" 1.1.1.1 de-ad-be-ef-de-ad
In Windows 2000, XP & 2003:
arp -s 1.1.1.1 de-ad-be-ef-de-ad
For MacOS X:
arp -S 1.1.1.1 de-ad-be-ef-de-ad
On Linux Systems:
arp -s 1.1.1.1 de:ad:be:ef:de:ad
One way to automate it to put in a startup script might be:
arp -s $(route -n | awk '/^0.0.0.0/ {print $2}') \
$(arp -n | grep `route -n | awk '/^0.0.0.0/ {print $2}'`| awk '{print $3}')
For Solaris:
arp -s 1.1.1.1 de:ad:be:ef:de:ad permanent
Source: http://www.securitybydefault.com/2010/10/como-anadir-una-entrada-estatica-en-la.html
thanks!!!
Monday, October 18, 2010
Change the background color in Gnome terminal and in Ubuntu
Command is: setterm -term linux -back blue -fore white -clear This quick tutorial will show you how to change the background color of gnome terminal. If you don’t like the current background color and want to change it, then I’ll show you how to change it to the color of your choice.
Getting started:
To change the background color, open gnome terminal and click Edit –> Preferences
Uncheck the box to ‘Use colors from system theme’, then choose the background color.
Close out.
Enjoy!
Thanks for reading and please come back soon.
Soure:
http://stackoverflow.com/questions/263892/change-the-background-color-in-gnome-terminal-through-a-command
http://www.liberiangeek.net/2010/07/change-the-background-color-of-gnome-terminal-in-ubuntu-10-04-lucid-lynx/
thanks!!!
Friday, October 15, 2010
Linux route command
Route command gives the possibility to specify static routes.
The syntax of the command is Unix flavour spific:
These methods of changing the route table don't last accross reboots. Listed below are methods to make any of these changes permanent.
Checking the route table in Linux
netstat -rn
route -r
Adding and Removing a Network in Linux
route add -net 10.10.10.0/24 gw 192.168.0.1
route del -net 10.10.10.0/24 gw 192.168.0.1
or
route add -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.1.253
route del -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.1.253
Adding and Removing a specific host is Linux-flavour specific:
route add -host 10.10.10.45 gw 192.168.0.1
route del -host 10.10.10.45 gw 192.168.0.1
Adding a Default GW in Linux
route add default gw 192.168.0.1
route del default gw 192.168.0.1
Note: The old gw will still remain and may need to be taken out for the system to function properly.
The routing information above is not persistent across reboots. After a reboot, the routing information will be lost and you need to add them in again.
To make the routing information persistent, add the “route add” line as seen above into the /etc/rc.local file.
Sample /etc/rc.local file.
#!/bin/sh
#
# This script will be executed *after* all the other init scripts.
# You can put your own initialization stuff in here if you don't
# want to do the full Sys V style init stuff.
touch /var/lock/subsys/local
route add -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.1.253
Making addition permanent
Routes are made permanent in Red Hat Linux by adding routes to /etc/sysconfig/static-routes
In Suse: Yast -> Network Devices -> Network card -> Edit -> Routing
Or edit /etc/sysconfig/network/routes if you prefer the CLI.
Soure:
http://thedaneshproject.com/posts/how-to-add-route-in-linux/
http://www.softpanorama.org/Net/Netutils/route_in_linux.shtml
thanks!!!
The syntax of the command is Unix flavour spific:
These methods of changing the route table don't last accross reboots. Listed below are methods to make any of these changes permanent.
Checking the route table in Linux
netstat -rn
route -r
Adding and Removing a Network in Linux
route add -net 10.10.10.0/24 gw 192.168.0.1
route del -net 10.10.10.0/24 gw 192.168.0.1
or
route add -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.1.253
route del -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.1.253
Adding and Removing a specific host is Linux-flavour specific:
route add -host 10.10.10.45 gw 192.168.0.1
route del -host 10.10.10.45 gw 192.168.0.1
Adding a Default GW in Linux
route add default gw 192.168.0.1
route del default gw 192.168.0.1
Note: The old gw will still remain and may need to be taken out for the system to function properly.
The routing information above is not persistent across reboots. After a reboot, the routing information will be lost and you need to add them in again.
To make the routing information persistent, add the “route add” line as seen above into the /etc/rc.local file.
Sample /etc/rc.local file.
#!/bin/sh
#
# This script will be executed *after* all the other init scripts.
# You can put your own initialization stuff in here if you don't
# want to do the full Sys V style init stuff.
touch /var/lock/subsys/local
route add -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.1.253
Making addition permanent
Routes are made permanent in Red Hat Linux by adding routes to /etc/sysconfig/static-routes
In Suse: Yast -> Network Devices -> Network card -> Edit -> Routing
Or edit /etc/sysconfig/network/routes if you prefer the CLI.
Soure:
http://thedaneshproject.com/posts/how-to-add-route-in-linux/
http://www.softpanorama.org/Net/Netutils/route_in_linux.shtml
thanks!!!
Thursday, October 14, 2010
My Project
Hi!
My project about Metasploit.
I'm going to transtlate Metasploit Unleased - Master the Framework and add some other funtions.
http://www.offensive-security.com/metasploit-unleashed/
http://www.4shared.com/file/Qrc0rhBU/List.html
It's finally time to restart !!!
A new journey begins ...!!!
My project about Metasploit.
I'm going to transtlate Metasploit Unleased - Master the Framework and add some other funtions.
http://www.offensive-security.com/metasploit-unleashed/
http://www.4shared.com/file/Qrc0rhBU/List.html
It's finally time to restart !!!
A new journey begins ...!!!
Subscribe to:
Posts (Atom)